[ad_1]

Getty Pictures
A safety researcher says that Apple’s iOS units do not absolutely route all community visitors by VPNs, a possible safety problem the gadget maker has identified about for years.
Michael Horowitz, a longtime pc safety blogger and researcher, places it plainly—if contentiously—in a continually updated blog post. “VPNs on iOS are damaged,” he says.
Any third-party VPN appears to work at first, giving the gadget a brand new IP tackle, DNS servers, and a tunnel for brand spanking new visitors, Horowitz writes. However classes and connections established earlier than a VPN is activated don’t terminate and, in Horowitz’s findings with superior router logging, can nonetheless ship knowledge outdoors the VPN tunnel whereas it is lively.
In different phrases, you’d anticipate a VPN to kill present connections earlier than establishing a connection to allow them to be re-established contained in the tunnel. However iOS VPNs cannot appear to do that, Horowitz says, a discovering that’s backed up by an identical report from Could 2020.
“Information leaves the iOS gadget outdoors of the VPN tunnel,” Horowitz writes. “This isn’t a traditional/legacy DNS leak, it’s a knowledge leak. I confirmed this utilizing a number of kinds of VPN and software program from a number of VPN suppliers. The most recent model of iOS that I examined with is 15.6.”
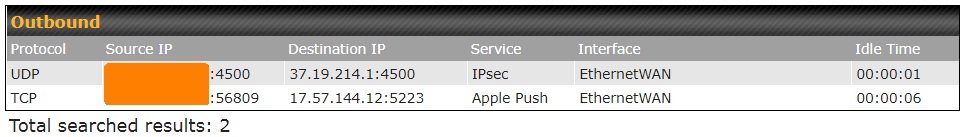
Safety blogger Michael Horowitz’s logs present a VPN-connected iPad reaching out to each his VPN supplier (37.19.214.1) and Apple Push (17.57.144.12). The Apple connection is outdoors the VPN and will doubtlessly expose his IP tackle if seen by an ISP or different events.
Privateness firm Proton beforehand reported an iOS VPN bypass vulnerability that began no less than in iOS 13.3.1. Like Horowitz’s publish, ProtonVPN’s weblog famous {that a} VPN sometimes closes all present connections and reopens them inside a VPN tunnel, however that did not occur on iOS. Most present connections will finally find yourself contained in the tunnel, however some, like Apple’s push notification service, can final for hours.
The first problem with non-tunneled connections persisting is that they might be unencrypted and that the IP tackle of the consumer and what they’re connecting to may be seen by ISPs and different events. “These at highest threat due to this safety flaw are individuals in nations the place surveillance and civil rights abuses are widespread,” ProtonVPN wrote on the time.
ProtonVPN confirmed that the VPN bypass continued in three subsequent updates to iOS 13. ProtonVPN indicated in its weblog publish that Apple would add performance to dam present connections, however this performance as added didn’t seem to make a distinction in Horowitz’s outcomes.
Horowitz examined ProtonVPN’s app in mid-2022 on an iPad iOS 15.4.1 and located that it nonetheless allowed persistent, non-tunneled connections to Apple’s push service. The Kill Swap perform added to ProtonVPN, which describes its perform as blocking all community visitors if the VPN tunnel is misplaced, didn’t forestall leaks, in line with Horowitz.
Horowitz examined once more on iOS 15.5 with a unique VPN supplier and iOS app (OVPN, operating the WireGuard protocol). His iPad continued to make requests to each Apple companies and to Amazon Internet Providers.
ProtonVPN had steered a workaround that was “nearly as efficient” as manually closing all connections when beginning a VPN: Connect with a VPN server, activate airplane mode, then flip it off. “Your different connections must also reconnect contained in the VPN tunnel, although we can not assure this 100%,” ProtonVPN wrote. Horowitz means that iOS’s Airplane Mode capabilities are so complicated as to make this a non-answer.
We have reached out to each Apple and OpenVPN for remark and can replace this text with any responses.
Horowitz’s publish does not provide specifics on how iOS may repair the difficulty. For his half, Horowitz recommends a $130 dedicated VPN router as a really safe VPN answer.
VPNs, particularly industrial choices, proceed to be a sophisticated piece of Web safety and privateness. Picking a “best VPN” has lengthy been a problem. VPNs may be introduced down by vulnerabilities, unencrypted servers, greedy data brokers, or by being owned by Facebook.
Source link



